Step 2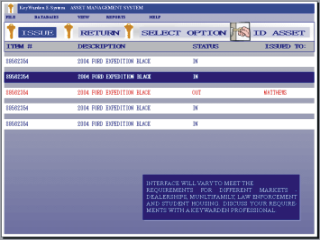
To See Sample Copies of Reports, Click Image.
Step 2: Granted access the user inputs the item number for the key(s) that they wish to access. If the key they are requesting is checked-out, they will be informed as to who has that key. Software Notes: The simple and intuitive Windows® interface is adapted for different markets such as auto dealerships, multi-family housing, law enforcement, or student housing. Interfacing to existing PC networks is easy to implement and trouble-free. This means that system operators can access the data at any time from a permitted workstation. Within these different markets, there are connectivity options to other vendors. For example, an interface to the Reynolds and Reynolds DMS system is available for auto dealerships. |