Step 2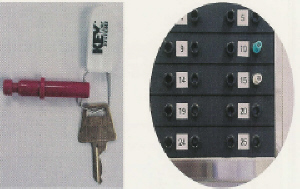
The key plug is release by the system.
3. Return the key to its port. A quarter turn to the left frees the user’s access peg. The key plug is once again locked onto the board. Simple, effective and affordable! |
2. Remove the key plug with its attached keys from the board.
The user’s access peg cannot be removed until the key plug is returned. Since the access peg is marked with an I. D. number, name, color, or letters, you know at a glance who has taken the keys! Quick Note: Since users can be assigned color-coded access pegs contractors, or other groups of users, can be issued a large volume of keys quickly and held accountable.
Step 3
The user’s Access Peg is locked in on that key slot until the key is returned. With a glance you will know who has which key.
Click Image to Download a Brochure.
|

